The Role of Content Delivery Networks (CDN) in DDOS Protection
As the incidents of DDOS attacks escalate with hosting servers flooded with massive and unmanageable traffic, throwing online presence into disarray, there is awareness about deploying efficient defence mechanisms to thwart such cyberattacks.
One crucial step for DDOS protection is implementing a cloud-based DDOS mitigation system to combat these cyber-attacks. In the defence against DDOS attack, efficient Content Delivery Networks (CDNs) play a vital role in augmenting DDOS protection.
Functional details of CDNs
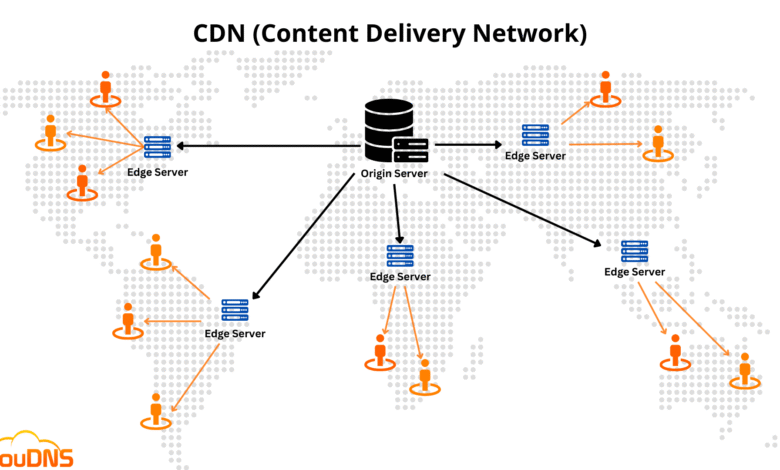
Let us take a look at how a CDN works. The term CDN stands for a group of servers distributed around the world. When a CDN is operational, the content of the hosted website will not be fully stored on the origin server. The brilliance is that copies of the content will be stored or cached across many servers.
This also alleviates the bandwidth pressure on the origin server, especially for high-traffic websites with users spread all around the globe.
CDN’s role in thwarting or minimizing DDOS attacks is achieved by distributing traffic across a global network of servers to ensure that malicious traffic is effectively diverted. This allows the operations of the origin server to go on despite the DDOS attack.
What makes CDN a go-to solution
The use of an efficient content delivery network (CDN) is a go-to strategy for battling DDOS attacks. Since the attack works around overloading a hosting server, CDNs have systems to mitigate the impact by distributing the load evenly across a series of geographically distributed servers.
Thanks to the operational structure of a CDN, it can easily redistribute traffic when necessary and act as an effective buffer against DDOS attacks.
The advantage is even if one server fails, many other servers will be operational. CDNs also handle certificate management in terms of automatic certificate generation and renewal.
How CDNs manage DDOS protection strategies
Important CDN providers are recognized for their 24/7 support and dedicated DDOS mitigation strategies, offering seamless expert assistance. Their robust and scalable solutions for DDOS protection utilize global infrastructure, advanced security features, and proactive monitoring.
They ensure websites remain operational even during attacks, preserving the best user experience and maintaining the reputation of the web property.
Many security features are also at work, including rate limiting, web application firewalls, and SSL/TLS encryption, to support enhanced DDoS protection.
CDNs are known for effective mechanisms to manage large volumes of traffic, including malicious traffic during DDoS attacks. They act as a buffer to absorb the intensity of the attack, ensuring the hosting server is protected from severe damage.
CDNs also have systems in place to block malicious requests before they reach the origin server, alleviating some of the load. Additionally, security features like rate limiting restrict the number of user requests within a specific time frame, preventing attackers from overwhelming the server with excessive requests.
Extra security features of CDNs
Some other prominent security features of CDNs also include the integration of Web Application Firewalls (WAFs) to boost protection against application-layer attacks.
In establishing secure connections, the SSL/TLS encryption of CDNs between the user and the stronger encryption between the CDN and the origin server escalate protection by many folds.
We know there exists some primary-level planning for DDOS mitigation, as in geo-blocking, IP blacklisting, and signature identification. Another important step is setting lower flood drop thresholds for SYN, UDP (User Datagram Protocol), and ICMP.
However, the threat scenario warrants advanced tech strategies that must align with the basic preparedness to combat DDOS attacks. CDNs are proactive with their extensive monitoring, utilizing sophisticated analytics and automation tools to respond to any DDOS attack.
This enables the detection of unusual traffic and the immediate routing and filtering of malicious traffic to mitigate the DDOS attack.
Constant vigil against DDOS attacks
Some notable DDOS attacks that made headlines include the GitHub attack in 2018, which sent the website offline for a considerable time. Similarly, the news giant BBC experienced a DDOS attack in 2015, affecting its entire network of websites.
South African banking websites faced serious assaults in 2019 when ransom-driven DDOS attacks targeted the banking sector.
To conclude
The number of DDoS attacks will only rise. Regardless of business size, when a website is down and compromised by orchestrated fake traffic, the losses can be substantial.
In addition to lost revenue and big damage to brand equity, if a business is appearing lethargic to fend off DDOS attacks and suffers a security breach, customers may refuse to associate with such businesses due to fears for their data security.
So, taking steps for DDoS protection means a lot, as a lot of things are at stake.
